What is TLS and what is its role in the Modbus-TCP version of the Modbus protocol?
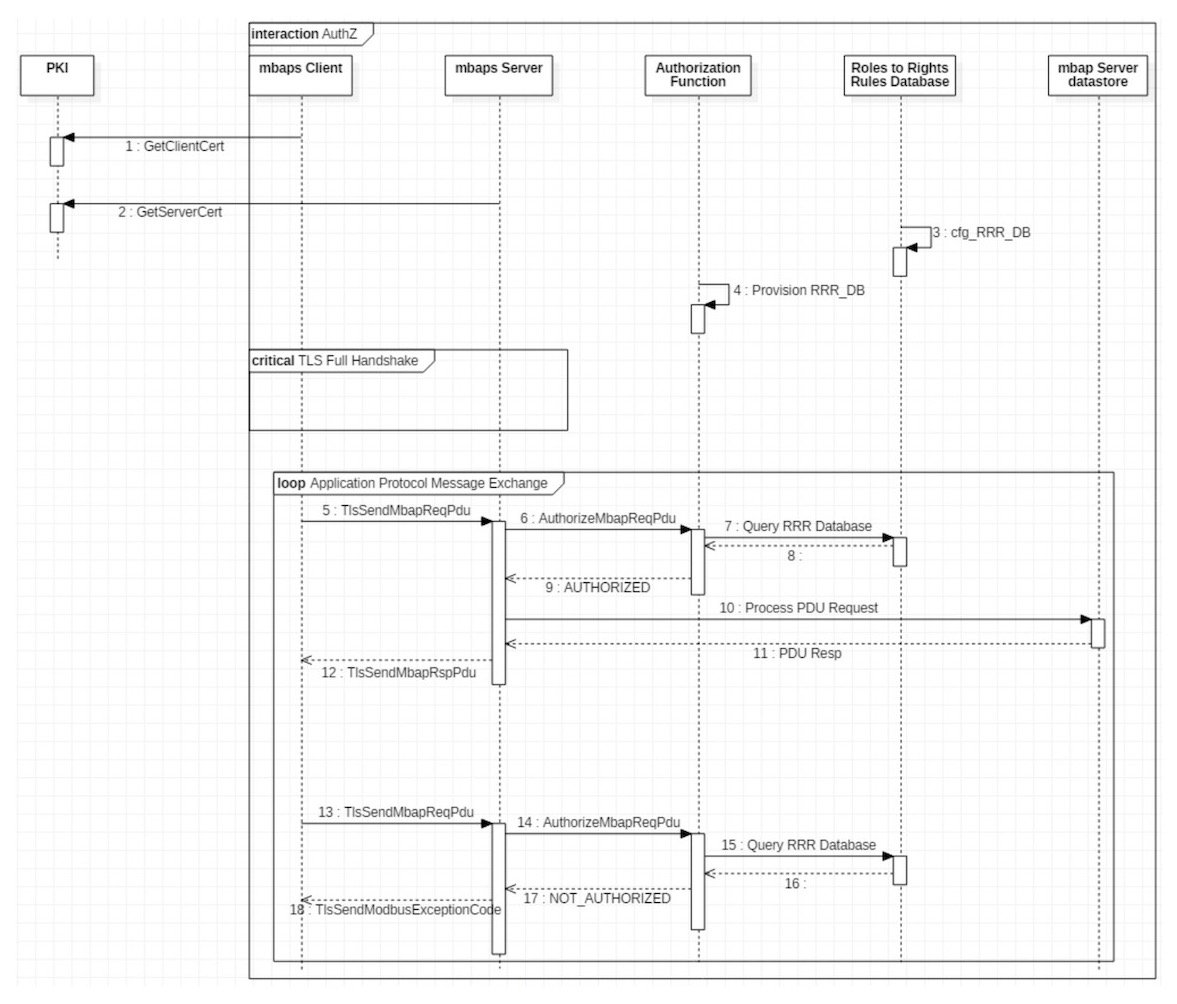
Security comes with added protocol complexity. Many industrial control systems rely upon encapsulating Modbus Application Protocol (MBAP) Protocol Data Unit (PDU) messages carried on a TCP/IP network within a “TLS” layer to secure communications. The combined solution is called ‘Modbus/TCP Security.’ This system enables the convergence of industrial operational systems with the nebulous IoT (internet of things) and a whole new class of devices referred to as ‘Industrial Internet of Things’ (IIoT) devices.
What is “TLS” exactly, how does it provide the security needed, and what are the potential weaknesses to consider?
TCP/Modbus security concept view.
What Is TLS?
The transport layer security (TLS) provides a secure communications channel between MBAP end devices. TLS 1.3 is the most recent update to the TLS protocol and feature a faster handshake (more on that below) and updates to encryption, algorithms, and ciphers.
TLS Protocol vs SSL Protocol
From a simplified perspective, TLS can be considered an improved and more secure/security-oriented version of the secure sockets layer (SSL) that were typically used in TCP systems in the past. Serious vulnerabilities were uncovered with SSL in this context, however, through a large number of malware and exploit attacks. Well-known examples include the ‘Browser Exploit Against SSL/TLS’ (BEAST), ‘Factored attack on RSA-Export Keys’ (FREAK) and the notorious Heartbleed bug.
These problems persist, so it is key to factor in security from day one if possible—or run the risk of having a hidden bomb in your infrastructure ready to go off.
Five years after the Heartbleed bug was discovered (even though it was well-publicized), there are still unpatched systems out in the wild allowing hackers to gain access to a device’s memory and potentially enabling discovery of crucial information like encryption keys.
TLS in Modbus Security
The TLS application layer is a vital addition to Modbus/TCP as it provides the necessary security mechanisms Modbus lacks.
Modbus/TCP Secure limits by specification TLS operation within requirements that ensure avoidance of known security vulnerabilities. The version must be TLS v1.2 or higher, not negotiate down to previous versions of TLS or use SSL3.0 or lower. Without this, systems like SCADA Modbus/TCP can suffer from severe protocol vulnerabilities.
Supervisory controls and data acquisition (SCADA) protocols incorporate an application messaging seventh layer in the OSI model. It is educational to consider potential attack mechanisms of such a system and how an integrated TLS layer is a solution.
TLS Handshake
Modbus/TCP sends messages as cleartext on a network and is easily intercepted and interpreted. Message efficiency is a weakness, exposing the control system to reconnaissance and making it easier for attackers to understand the network and potential vulnerabilities. The TLS protocol incorporates a sequence called the TLS Handshake, utilizing a public key cryptography-based cipher suite to encode sessions between devices. A Message Authentication Code (MAC) sent to information receivers ensures the integrity of data, preventing things like ‘man in the middle’ attacks from being successful.
These codes also provide message integrity checks, preventing false message injection into the control system, which can result in potentially devasting and expensive consequences. Imagine if pumps and valves were turned on in the wrong order in a chemical plant!
Addressing Human Error in Cybersecurity
It’s easy to focus on hackers and outside attackers—but security vulnerabilities include employee, programming, or configuration errors caused by people doing the wrong thing accidentally or maliciously. It could be the right people doing the right thing at the wrong time!
The way around this is a secure authentication process, but none is built into the low levels of the protocol. TLS handles authentication through the TLS Handshake process. During a handshake, the two communicating devices exchange acknowledgment messages to each other, verify each other’s permissions, and establish the previously-mentioned encryption protocols.
One benefit not usually considered is non-repudiation/accountability, as authentication ensures no one can deny that an action took place, mitigating the risk of dispute in tampering, misuse or system changes. Responsibility brings confidence to the validity of issue tracing and auditing and fosters high-quality standards in system operation and maintenance.
TCP Packets for Data Delivery
Security implies reliability. Reliability means several things, including not just delivery of data but the delivery of the right data, once and in a time-frame required by the system.
TCP packets are reordered in the correct sequence by protocol and retransmitted if lost, but they are also ‘best effort’ packets with no expectation of reduction of jitter (variance of delay).
TLS does not require packets to be transmitted as TCP; it only requires a reliable transport layer protocol. However, UDP is an example of a protocol that is not reliable because it focuses on real-time delivery of data over the successful transporting every packet.
Considering this, TLS does not ‘in itself’ provide a solution to solve this problem. In the future, protocols like ‘Datagram Transport Layer Security’ (DTLS) may come into the picture, which uses UDP and overcomes another severe problem—TCP Meltdown. Meltdown occurs when stacked protocols attempt to compensate for errors and the resulting error correction causes overcompensation, leading to delays.
TLS Security and How It Works
The TLS layer prevents an attacker from performing reconnaissance activity on the targeted network. Privacy is essential because, without this, a SCADA Modbus slave device may return illegal function exception responses if the attacker sends a query that contains an unsupported function code. Authentication prevents a remote attacker from using this mechanism to carry out surveillance.
TLS mitigates the lack of robust security checking process in the SCADA Modbus/TCP protocol as it does not include a mechanism for validating communication between the Modbus master and slave devices, themselves. It prevents an attacker from issuing arbitrary commands to any slave device using a Modbus master. A similar attack vector can see a remote hacker using invalid address queries to gather network information from network host returned messages.
DoS Attacks
SSL/TLS style protocols face always face the threat of a Denial of Service Attacks (DoS). DoS can appear in many forms, one such being it is possible to create a situation known as an Exhaustion Attack, bombarding the protocol stack to make it run out of memory and processing resources due to the number of renegotiations occurring. One can disable renegotiation in the stack, or invest in an accelerator to provide more margin.
DoS is an ongoing issue, but what TLS does enable is protection for low-level Modbus TCP vulnerabilities. An example of a DoS scenario is an attacker sending malicious or spurious data field values. The resulting traffic congestion could cause control information not to be transferred between devices at critical times. Adding a TLS layer as a level of abstraction avoids packet length exploits caused by Modbus’s small maximum legal packet size limit of 260 bytes through the added TLS layer by ensuring that the ‘long packet length’ problem does not cause buffer overflows in devices—and once again DoS effects.
Conclusion
The TLS application layer provides an excellent way of adding an industry standardized, robust security and authentication cryptographically protected Modbus/TCP solution. Using Modbus/TCP Security based upon TLS is a practical way of meeting today’s cybersecurity threat. In the future, we may see this protocol develop to enable support for TLS on other transport layer protocols, or variations of the TLS protocol to factor in lower reliability in the transport layer.
A better understanding of its advantages and limitations will allow for better system architecture. Still, no matter how robust your strategy is, it is important to remember that it will never replace a sturdy door, a solid lock, and a security guard. When an attacker gains access to your local network—all bets are off!
Copyright Statement: The content of this website is intended for personal learning purposes only. If it infringes upon your copyright, please contact us for removal. Email: [email protected]
